위키 구독하기
Share wiki
Bookmark
Trusted Execution Environments
에이전트 토큰화 플랫폼 (ATP):에이전트 개발 키트(ADK)로 자율 에이전트 구축
0%
Trusted Execution Environments
**신뢰 실행 환경(TEE)**은 기밀성과 무결성을 고려하여 코드와 데이터를 보호하도록 설계된 컴퓨터 메인 프로세서 내의 안전하고 격리된 영역입니다. 엔클레이브라고도 하는 TEE는 호스트 시스템의 운영 체제, 하이퍼바이저 및 기타 애플리케이션으로부터 중요한 계산을 분리하는 하드웨어로 강화된 장벽을 제공하여 시스템에 대한 모든 제어 권한을 가진 관리자로부터도 데이터를 보호합니다. [1] [2]
개요
신뢰 실행 환경(Trusted Execution Environment)의 핵심 목적은 코드의 안전한 실행과 데이터의 기밀 처리를 가능하게 하는 것입니다. 이는 하드웨어 수준의 격리를 통해 달성되며, 호스트 운영 체제를 포함하여 엔클레이브 외부의 모든 소프트웨어에서 접근할 수 없는 보호된 컨테이너를 생성합니다. TEE의 보안은 일반적으로 제조 중에 프로세서에 내장된 변경 불가능한 개인 키를 포함하는 "하드웨어 루트 오브 트러스트(hardware root of trust)"에 의해 고정되어 환경이 사용자 제어 소프트웨어에 의해 시뮬레이션되거나 손상되는 것을 방지합니다. [3]
이 기술은 디지털 권한 관리(DRM) 및 안전한 결제와 같은 애플리케이션을 위해 1990년대에 처음 등장했습니다. [1] 이 개념은 2000년대 중반에 OMTP(Open Mobile Terminal Platform)에서 "Advanced Trusted Environment: OMTP TR1" 표준으로 보다 공식적으로 정의되었습니다. [3] 최근 몇 년 동안 TEE는 블록체인 및 Web3 분야에서 개인 정보 보호를 구현하고, 확장성을 향상시키며, MEV(Maximal Extractable Value)와 같은 보안 위험을 완화하기 위한 실용적인 솔루션으로 상당한 주목을 받고 있습니다. [4]
TEE는 종종 영지식 증명 (ZKP) 및 완전 동형 암호화(FHE)와 같은 순수하게 암호화 기반 개인 정보 보호 솔루션과 비교됩니다. ZKP는 수학적 증명에 기반한 "신뢰 없는(trustless)" 모델을 제공하는 반면, TEE는 하드웨어 제조업체에 대한 신뢰에 의존합니다. 그러나 TEE는 일반적으로 범용 컴퓨팅에 더 적합하고 유연한 것으로 간주되며, 맞춤형 도메인 특정 언어 또는 복잡한 증명 시스템 없이 기존 애플리케이션을 실행할 수 있습니다. [1] [3]
기술
핵심 원칙
TEE의 기능은 안전한 컴퓨팅 환경을 제공하는 여러 핵심 원칙을 기반으로 구축됩니다.
- 기밀성: TEE 내부에 로드된 코드와 데이터는 메모리에서 암호화됩니다. 호스트 운영 체제, 커널 또는 하이퍼바이저를 포함하여 엔클레이브 외부의 모든 소프트웨어에서 액세스할 수 없습니다.
- 격리: 하드웨어 수준의 분리를 통해 호스트 시스템이 TEE 내부에서 실행되는 프로세스에 액세스하거나 간섭하는 것을 방지합니다. TEE는 엄격한 메모리 액세스 제어를 적용하며 호스트 OS가 TEE의 보호된 메모리를 읽으려고 시도하면 하드웨어에서 차단합니다.
- 증명 가능성: TEE는 원산지와 실행 중인 정확한 코드에 대한 암호화 증명인 "증명"을 생성할 수 있습니다. 이를 통해 원격 제3자는 신뢰할 수 있고 변조되지 않은 소프트웨어를 실행하는 정품 TEE에서 계산이 수행되었는지 확인할 수 있습니다. [1]
작동 메커니즘
TEE 내에서 코드와 데이터의 라이프사이클은 부팅부터 종료까지 보안을 보장하기 위해 여러 하드웨어 관리 단계를 거칩니다.
- 초기화: 시스템 부팅 시 BIOS/UEFI는 하드웨어를 초기화하고 TEE를 위한 메모리 영역을 할당합니다. 전용 메모리 암호화 엔진(MEE)은 이 RAM 영역을 암호화합니다.
- 로딩: 암호화된 코드와 데이터는 스토리지에서 TEE의 보호된 메모리로 로드되며, 엔클레이브 내에서만 사용하기 위해 해독됩니다.
- 실행: 애플리케이션은 특수 CPU 명령어를 사용하여 엔클레이브에 진입하며, 이는 기존 운영 체제에서 사용자 모드에서 커널 모드로 전환하는 것과 유사한 프로세스입니다.
- 상호 작용: 스토리지 및 네트워크 카드와 같은 주변 장치는 TEE의 신뢰 경계 외부에 있으므로 모든 I/O 작업은 공유 메모리를 통해 처리됩니다. 이러한 신뢰할 수 없는 구성 요소에서 TEE로 들어오는 데이터는 유효성을 검사해야 합니다. 보안 네트워크 통신을 위해 TEE는 자체 키 쌍을 내부적으로 생성하여 전송 계층 보안(TLS) 세션을 설정할 수 있습니다.
- 종료: TEE는 보안 API 또는 종료 기능을 사용하여 비 TEE 리소스와 상호 작용합니다. [1]
원격 증명
원격 증명은 TEE가 원격 당사자에게 무결성을 증명할 수 있도록 하는 중요한 기능입니다. 이 프로세스는 일반적으로 네 단계로 구성됩니다.
- 측정: CPU는 부트 펌웨어, 운영 체제 및 애플리케이션 바이너리를 포함하는 신뢰 컴퓨팅 기반을 측정합니다.
- 저장: 이 측정값은 CPU 내의 보안 하드웨어 레지스터에 저장됩니다.
- 서명: CPU는 제조 중에 하드웨어에 내장된 고유한 개인 증명 키를 사용하여 측정값에 서명합니다.
- 검증: 서명된 측정값 또는 "증명 보고서"가 원격 검증자에게 전송됩니다. 검증자는 서명을 확인하여 엔클레이브의 진위성을 확인하고 올바른 코드가 실행되고 있는지 확인할 수 있습니다. [2]
주요 구현
몇몇 주요 하드웨어 제조업체들이 자체적인 TEE 기술을 개발했습니다:
- Intel: Software Guard Extensions (SGX) 및 후속 기술인 Trust Domain Extensions (TDX).
- AMD: Secure Encrypted Virtualization (SEV).
- ARM: Confidential Compute Architecture (CCA).
- NVIDIA: Hopper 및 Blackwell GPU 아키텍처의 Enclaves. [1]
사용 사례
전통적인 애플리케이션 및 Web2 애플리케이션
블록체인에 도입되기 전에 TEE는 민감한 데이터와 지적 재산을 보호하기 위해 다양한 분야에서 널리 사용되었습니다.
- 디지털 권리 관리(DRM): 4K 영화 및 프리미엄 오디오와 같은 고가치 콘텐츠를 무단 복사로부터 보호합니다.
- 금융 서비스: 모바일 지갑, 비접촉식 결제 및 POS(Point-of-Sale) 단말기를 보호합니다.
- 인증: iPhone의 Apple Secure Enclave와 유사하게 얼굴 인식, 지문 스캔 및 음성 인증을 포함한 생체 데이터 처리를 위한 안전한 환경을 제공합니다.
- 기업 및 정부: 모바일 장치 및 서버 인프라에서 기밀 정보를 안전하게 처리합니다. [3] [5]
Web3 및 블록체인 애플리케이션
TEE는 개인 정보 보호, 확장성 및 보안을 포함하여 블록체인 공간의 여러 주요 과제에 대한 솔루션을 제공합니다. 2025년 9월 현재 50개 이상의 팀이 TEE 기반 블록체인 프로젝트에서 활발히 활동하고 있는 것으로 보고되었습니다. [2]
프라이빗 스마트 컨트랙트
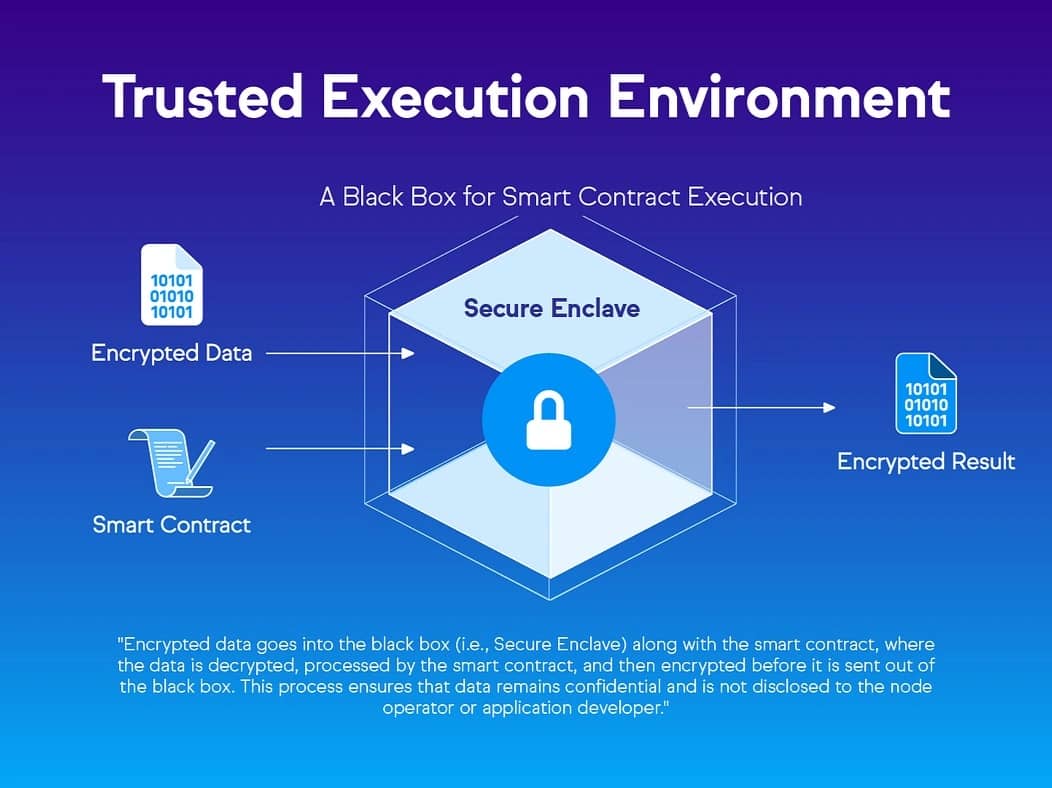
TEE를 사용하면 로직, 데이터 입력 및 상태가 공개적으로, 심지어 네트워크를 실행하는 노드 운영자에게도 비공개로 유지되는 기밀 스마트 컨트랙트를 생성할 수 있습니다. 이를 통해 의료 또는 금융 데이터와 같은 민감한 정보를 온체인에서 처리하는 애플리케이션이 가능합니다. 노드 운영자의 TEE는 데이터 자체에 액세스하지 않고도 이 개인 데이터에 대한 계산을 실행할 수 있습니다. [1]
"TEE를 사용하면 노드 운영자가 서버에서 처리되는 개인 데이터에 대한 지식 없이 네트워크에 참여할 수 있습니다." [1]
확장성 및 오프체인 연산
연산 집약적인 작업은 메인 블록체인에서 TEE 지원 노드로 오프로드할 수 있습니다. 이러한 노드는 작업을 안전하게 오프체인에서 실행하고 결과와 정확한 실행 증명만 체인으로 다시 제출합니다. 이는 네트워크 부하와 트랜잭션 비용을 줄여 처리량을 증가시킵니다. 이 모델은 일부 레이어 2 확장 솔루션 및 분산 클라우드 컴퓨팅 플랫폼에서 사용됩니다. [3]
MEV 완화
최대 추출 가능 가치(MEV)는 트랜잭션을 재정렬, 삽입 또는 검열하여 블록체인에서 추출할 수 있는 이익을 의미합니다. TEE는 개인 트랜잭션 풀과 검증 가능한 블록 빌더를 생성하여 MEV에 대처하기 위해 구현되고 있습니다. 이러한 시스템에서 사용자는 TEE 내부에서 작업을 실행하는 블록 빌더에게 트랜잭션을 제출합니다. TEE는 트랜잭션 데이터가 블록에서 완료될 때까지 기밀로 유지되도록 하여 MEV 검색자가 트랜잭션을 선점하거나 샌드위치 공격하는 것을 방지합니다. 이 접근 방식은 빠르고 분산되어 있으며 개인 정보 보호가 가능한 시스템을 만들어 "MEV 삼중고"를 해결하는 것을 목표로 합니다. [5]
보안 오라클 및 상호 운용성
TEE는 오라클 연산을 위한 안전한 환경을 제공하여 스마트 계약에 제공되는 외부 데이터의 무결성을 보장할 수 있습니다. 또한 서로 다른 블록체인 네트워크 간의 안전한 데이터 교환 및 자산 전송을 용이하게 하여 크로스 체인 상호 운용성을 향상시키는 신뢰할 수 있는 중개자 역할을 할 수 있습니다. [3]
구현 및 채택
Web3 생태계 전반에 걸쳐 수많은 프로젝트가 TEE를 아키텍처에 통합했습니다.
- Secret Network: Intel SGX를 사용하여 기본적으로 개인 스마트 계약을 시작한 최초의 블록체인입니다. Cosmos SDK로 구축되었으며 기밀 상태 및 트랜잭션을 지원합니다.
- Oasis Network: TEE를 사용하여 기밀 EVM 호환 ParaTime인 Sapphire를 구동하여 Ethereum과 유사한 환경에서 개인 dApp을 사용할 수 있도록 하는 플랫폼입니다.
- Unichain: Uniswap 팀에서 개발한 낙관적 롤업으로 2024년 10월에 출시되었습니다. Flashbots와 협력하여 MEV 저항 인프라를 만들기 위해 블록 구축 프로세스에서 TEE(초기에는 Intel TDX)를 사용합니다.
- Flashbots: TEE를 활용하는 "검증 가능한 블록 빌더"(롤업 부스트)를 개발하는 MEV에 중점을 둔 연구 조직입니다. 이 기술은 Unichain 설계의 핵심 구성 요소입니다.
- iExec: 안전한 오프체인 컴퓨팅을 위해 Intel SGX를 사용하는 분산형 클라우드 컴퓨팅 플랫폼입니다.
- Scroll 및 Taiko: Ethereum 롤업은 TEE를 ZK 증명자와 함께 두 번째 유형의 증명자로 사용하여 중복성을 추가하고 보안을 강화합니다. 기타 주목할 만한 프로젝트로는 Cycles Protocol, Automata, Phala 및 Marlin이 있습니다. [2] [5] [4]
과제 및 제한 사항
TEE는 유용성에도 불구하고 보안 모델 및 중앙 집중식 하드웨어에 대한 의존성과 관련된 중요한 과제와 비판에 직면해 있습니다.
공급업체 신뢰 및 중앙 집중화
TEE의 전체 보안 모델은 하드웨어 제조업체(예: Intel, AMD)에 대한 신뢰에 의존합니다. 이는 중앙 집중화된 실패 지점을 도입하고 많은 블록체인 프로젝트의 탈중앙화 정신에 위배됩니다. 제조업체가 정부 기관에 의해 백도어를 도입하도록 강요받거나 복잡한 공급망에서 결함이 발생할 위험이 있습니다. [2] [3]
보안 취약점
TEE는 기밀성 및 무결성 보장을 손상시킬 수 있는 여러 종류의 공격에 취약한 것으로 입증되었습니다.
- 측면 채널 공격: 이러한 공격은 하드웨어 작동 패턴을 관찰하여 정보를 추출합니다. 예로는 투기적 실행을 악용하는 Spectre와 CPU 전압을 조작하여 SGX 엔클레이브 내부에 결함을 유도하고 비밀을 추출하는 Plundervolt가 있습니다.
- 마이크로프로세서 취약점: TEE는 Meltdown과 같은 일반적인 하드웨어 버그에 취약합니다.
- 물리적 공격: 연구에 따르면 기존 TEE 설계는 칩에 대한 물리적 접근 권한이 있는 정교한 공격자를 완전히 방어할 수 없습니다.
- 구현 버그: TEE의 격리 메커니즘 또는 내부에서 실행되는 소프트웨어의 결함으로 인해 보안이 손상될 수 있습니다. 예를 들어 Intel의 SGX 기술은 "sgx.fail"과 같은 웹사이트에 기록된 취약점 기록이 있습니다. [1] [5]
Blockworks Research의 Daniel Shapiro는 Unichain과 같은 프로토콜의 위험에 대해 언급하면서 "체인이 성장함에 따라 공격에 대한 인센티브도 함께 증가합니다. 사용자 자금을 위험에 빠뜨릴 수 있는 새로운 보안 악용이 발생할 수 있습니다."라고 말했습니다. [5]
위험 완화 및 연구
TEE의 내재적 한계를 해결하기 위해 개발자와 연구자들은 다양한 완화 전략을 제안하고 차세대 설계를 모색하고 있습니다.
구현을 위한 모범 사례
개발자는 TEE가 결국 손상될 수 있다는 가정 하에 시스템을 설계하는 것이 좋습니다.
- 실패를 고려한 설계: 시스템은 TEE 익스플로잇이 "실존적 위험이 아닌 성가신 일"이 되도록 설계해야 합니다. 예를 들어 TEE는 시스템의 무결성을 보호하는 유일한 구성 요소가 아니어야 합니다.
- 무결성보다 개인 정보 보호: TEE는 기밀성에 더 적합합니다. 트랜잭션 유효성 검증과 같은 무결성이 중요한 작업에 대한 유일한 메커니즘으로 사용하는 것은 권장되지 않습니다. 손상이 발생하면 공격자가 자산을 위조할 수 있기 때문입니다.
- Oblivious RAM (ORAM): 이 기술은 TEE가 호스트 RAM과 상호 작용할 때 메모리 액세스 패턴을 가려 성능 저하를 감수하면서 사이드 채널 누출을 완화하는 데 사용할 수 있습니다.
- Forward Secrecy 및 키 순환: 암호화 키를 정기적으로 교체하면 손상의 영향을 제한할 수 있습니다. 훔친 키는 이전 키로 보호된 과거 데이터를 해독하는 데 사용할 수 없기 때문입니다. [1]
분산 키 관리
단일 실패 지점을 방지하기 위해 TEE 기반 시스템은 분산 키 관리를 사용하는 경우가 많습니다. Ekiden 프로토콜은 신뢰할 수 있는 노드로 구성된 '키 관리 위원회'(KMC)가 임계값 암호화를 사용하여 중요한 키를 관리하는 모델을 개척했습니다. KMC는 개별 작업자 노드에게 짧은 수명의 제한된 액세스 키를 발급하며, 작업자 노드는 키를 받기 위해 원격 증명을 통해 합법성을 증명해야 합니다. 이 시스템에는 보안을 더욱 강화하기 위한 사전 예방적 키 순환이 포함됩니다. [2]
향후 연구 방향
제조사를 신뢰할 필요가 없는 TEE를 개발하기 위한 연구가 진행 중입니다. 제안된 해결책으로는 PUF(Physical Unclonable Functions)를 사용하여 신뢰의 근원을 확보하고, 마스킹 기술을 통합하여 물리적 공격으로부터 연산을 보호하며, 오픈 소스 하드웨어와 공식적으로 검증되고 재현 가능한 빌드를 사용하여 설계 무결성을 보장하는 TEE를 구축하는 것이 있습니다. [4]
잘못된 내용이 있나요?