Subscribe to wiki
Share wiki
Bookmark
Distributed Ledger Technology (DLT)
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
0%
Distributed Ledger Technology (DLT)
Distributed ledger technology (DLT) refers to the protocols and supporting infrastructure that allow computers in different locations to propose and validate transactions and update records in a synchronized way across a network.[2]
Tech
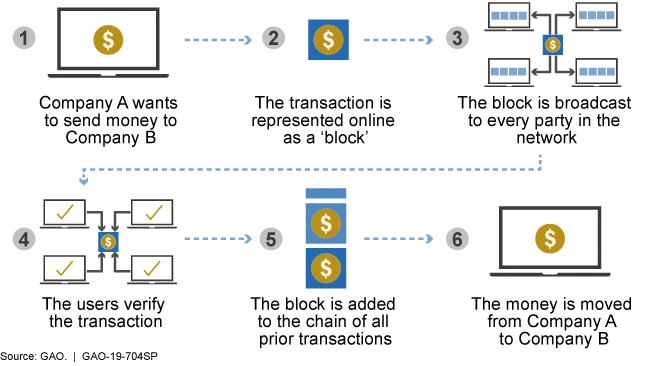
Transactions or data entries in a node are created by participants on the network. These transactions can represent various types of information, like, financial transactions, supply chain data, and voting records. Each transaction is broadcast to all nodes in the network. These nodes can be located anywhere and are part of a distributed network.
Nodes on the network independently verify the transaction's validity based on predefined rules and protocols. Verification typically involves checking the digital signatures, ensuring that the sender has the necessary permissions, and confirming that the transaction adheres to the network's rules.
To add a verified transaction to the ledger, the network must reach a consensus. Different DLTs use different consensus mechanisms, such as PoW, PoS, BFT, and, more. These mechanisms ensure that a majority of nodes agree on the transaction's validity before it is added to the ledger. Once consensus is reached, the verified transaction is added to a block. This block contains a group of transactions and is linked to the previous block in chronological order, forming a chain of blocks, called a blockchain.
Once a transaction is added to the ledger, it becomes immutable and tamper-resistant. It is nearly impossible to alter or delete the information without consensus from the network, making the ledger highly secure and reliable. Copies of the ledger are maintained on each node in the network. This redundancy ensures that even if some nodes go offline or are compromised, the ledger's integrity remains intact.
The distributed ledger continues to operate, adding new blocks of transactions in a continuous manner. This ensures a complete and transparent record of all transactions or data entries since the ledger's inception.[5]
Types of DLTs
Blockchain
In this type of DLT, transactions are stored in the form chain of blocks and each block produces a unique hash that can be used as proof of valid transactions. Each node has a copy of the ledger which makes it more transparent.
Permissioned DLT
Nodes have to take permission from a central authority to access or make any changes in the network. Mostly these types of permissions include identity verification.
Hyperledger Fabric is a permissioned DLT, designed for private and consortium blockchains, where access to the network is controlled and limited to trusted entities. Participants must be granted permission to join and interact with the network.
Permissionless DLT
There is no central authority to validate transactions, rather existing nodes are collectively responsible for validating the transactions. Various consensus mechanisms are used to validate transactions based on predefined algorithms. In the case of Bitcoin proof of work consensus mechanism is used.
Bitcoin operates on a public and permissionless blockchain, which means it is open for anyone to participate in the network without needing permission.
Hybrid DLT
It is combined with both permissionless and permissioned DLTs and can benefit from both of them.
Corda Enterprise is a hybrid DLT project, that allows organizations to create private, permissioned networks where participants are known and trusted. This is particularly valuable in industries where strict data privacy and regulatory compliance are essential, such as finance and healthcare.
Directed Acyclic Graph (DAG)
DAG employs a unique data structure to organize its data, leading to enhanced consensus. In this form of DLT, transaction validation largely hinges on the support from the majority of the nodes in the network. Every node is obligated to provide proof of transactions on the ledger before initiating any transactions. In this system, nodes must verify at least two prior transactions on the ledger to authenticate their own transaction.
IOTA is a public distributed ledger that uses a directed acyclic graph (DAG) structure known as the Tangle to store transactions.[1]
DLT Consensus Mechanisms
Proof of Work (PoW)
In PoW, miners compete to solve complex mathematical problems to validate transactions and create new blocks. The essence of PoW is that miners must make a financial investment and commit resources to validate transactions, providing them with an incentive.[3]
PoW is used by Bitcoin and Dogecoin for their BTC and DOGE cryptocurrencies.[7]
Proof of Stake (PoS)
In PoS, validators hold a stake in the network and are chosen to validate transactions based on the amount of the stake they hold. Seen as a more environmentally friendly option, PoS is at greater risk of a 51% attack.[3]
Projects that use PoS include Ethereum 2.0, Cardano, Tezos, and Polkadot.
Delegated Proof of Stake (DPoS)
DPoS is a variant of PoS, where the network selects a limited number of validators to validate transactions. This variation reduces the computational resources required to secure the network.[3]
Projects that use DPoS include BitShares, TRON, Steem, Lisk, Ark, and EOS.[6]
Byzantine Fault Tolerance (BFT)
In BFT, validators agree on a consensus value based on a voting system. This mechanism strives to avoid the Byzantine Generals Problem which describes a game theory problem where decentralized parties must arrive at a consensus by leveraging a trusted central party.[3]
Projects that use BFT include Hyperledger Fabric, Stellar, NEO, and Ripple.
Centralized vs Distributed Ledgers
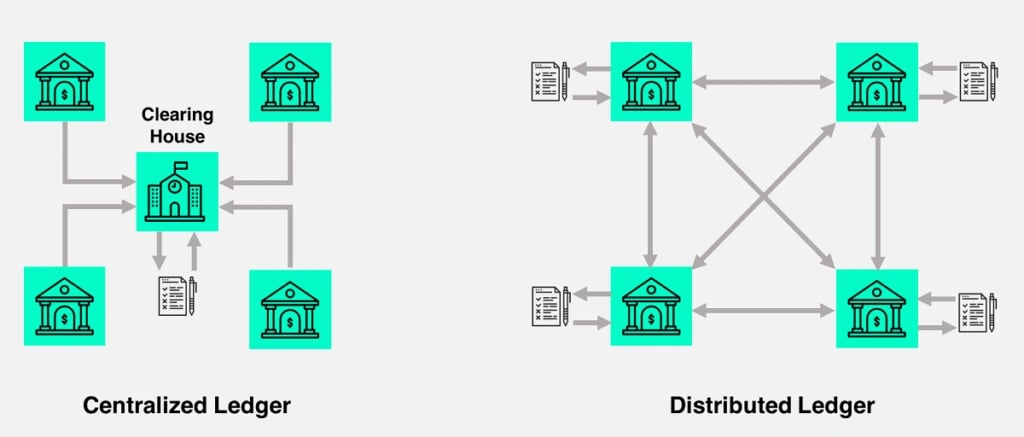
| Ledgers / Characteristics | Centralized Ledger | Distributed Ledger |
|---|---|---|
| Control | A single entity or authority has complete control over the ledger. This entity is responsible for maintaining, updating, and managing the ledger. | No single central authority. Data is distributed across a network of nodes, and no single entity has complete control over the ledger. |
| Trust | Trust is placed in the reputation and integrity of the central entity. | Trust is placed in the system's rules and algorithms, based on calculations, cryptography, and the consensus of the network. |
| Access | Only authorized individuals or entities are granted permission to view or modify the ledger. | Anyone can participate in the network, view the ledger, and validate transactions. |
| Transparency | Less transparent. Access to data is typically limited to what the authority deems necessary. | Highly transparent. Transaction data is visible to all participants, and the ledger's history is immutable and tamper-resistant. |
| Efficiency | Efficient and fast because there is a single point of control and decision-making. Transactions and data updates can be processed quickly. | Efficiency can vary. Some ledgers prioritize security and decentralization over speed, resulting in slower transaction processing. Others aim to improve scalability and transaction speed. |
| Resilience | Vulnerable to single points of failure. If the central authority experiences issues or is compromised, the entire ledger's integrity is at risk. | Resilient to failures and attacks. There is no single point of failure, making the ledger more robust and secure. |
| Examples | Traditional banking systems, government records, and corporate databases | Bitcoin, Ethereum, Hyperledger Fabric, etc |
Applications of DLT
DLT has found applications across various sectors, transforming industries and processes:
Finance
Cryptocurrencies like Bitcoin and Ethereum utilize blockchain, a type of DLT, to enable decentralized digital currency transactions, bypassing traditional financial intermediaries.
Supply Chain Management
DLT enhances transparency and traceability in supply chains by recording each step of a product's journey. This is particularly useful in verifying the authenticity of goods and reducing fraud.
Healthcare
Patient records, pharmaceutical supply chains, and clinical trials benefit from DLT's secure and immutable data storage, ensuring privacy and data integrity.
Voting Systems
DLT can be used to create secure and transparent voting systems, reducing the risk of election fraud and ensuring the integrity of democratic processes.
Real Estate
Property transactions often involve complex paperwork and intermediaries. DLT can simplify this process by securely recording and transferring property titles.
Cross-Border Payments
DLT can facilitate faster and more cost-effective cross-border payments by eliminating intermediaries and reducing transaction fees.[4]
DLT under the Law
DLT usually allows entities to transact without the need for external mechanisms for conflict resolution. But, the DLT-based service always remains subject to the legal and regulatory framework of the relevant jurisdiction. In Australia, as in many jurisdictions, there are scenarios where the legal system does not permit the enforcement of a contract solely on its terms.
For example, insolvency laws provide for clawback of transactions in certain circumstances, even where the contract in question may have contemplated those transactions occurring. It will be important to ensure that the DLT-based service is able to operate within the law.[8]
See something wrong?
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
