Hardware Wallet
A Hardware Wallet is a physical device that stores private keys offline, making them highly secure and resistant to hacking and cyber-attacks. It's a type of cold wallet, resembling a typical USB stick, designed specifically for storing cryptocurrencies. This wallet allows users to trade directly from it, rather than depositing into an exchange wallet.[1][2]
Overview
A crypto hardware wallet is a device that stores the private keys of a user's cryptocurrency assets in a secure chip. It allows the user to access and manage crypto without exposing keys to online threats. A crypto hardware wallet is also known as a cold wallet because it is not connected to the internet.
With a hardware wallet, transactions are signed within the device itself using a "crypto bridge", a straightforward software component that facilitates the hardware wallet's connection to the blockchain. When a user connects their hardware wallet to a PC, the crypto bridge sends unsigned transaction data to the device. The hardware wallet owner then signs the transactions with its private key and sends them back to the bridge, which subsequently broadcasts them to the entire blockchain network as finalized transactions. Importantly, at no point in this process does the user's private key leave or get transmitted outside the hardware wallet.[3][2]
Key Features
- Offline Storage: When not in use, the wallet remains disconnected from the internet, making it resistant to online hacking attempts. This cold storage is a key defense against the threat of cyberattacks.
- Secure Element: Hardware wallets are incorporated with hardware components specifically designed to safeguard cryptographic keys. These chips are tamper-resistant, making it difficult for malicious actors to compromise the security of the wallet.
- PIN or Password Protection: This layer of security ensures that even if the device falls into the wrong hands, unauthorized access is nearly impossible.
- Backup and Recovery: Hardware wallets provide a recovery seed or mnemonic phrase, usually consisting of 12 or 24 words. With this seed phrase, access to funds on a new device can be restored.
- Transaction Confirmation: A hardware wallet typically requires the user to verify and approve transactions on the device's screen. This step ensures that the user has full control over their funds and can review and confirm each transaction before it's finalized.
Types
The main and basic types of hardware wallets are as follows.[5][8]
- USB-Based Hardware Wallets: The most common type of hardware wallets are small, portable devices that connect to a computer or mobile device via USB. Examples include the Ledger Nano S, Ledger Nano X, and Trezor Model T.
- Bluetooth Hardware Wallets: Bluetooth hardware wallets offer wireless connectivity to computers or mobile devices, granting enhanced flexibility in terms of compatibility and ease of use. An example is the Ledger Nano X.
- Smartcard-Based Hardware Wallets: Hardware wallets designed in the form of smartcards resemble credit cards or security tokens. They are typically used with a card reader to access cryptocurrency funds. Examples of such wallets include the CoolWallet S and Cobo Vault.
- Metal Seed Storage: While not traditional hardware wallets, these are physical devices specifically designed to securely store the recovery seed (mnemonic phrase). Made from metal or other robust materials, they protect the recovery seed from physical damage, water, and fire. Examples include CryptoSteel and Billfodl.
- Paper Wallets: Certain hardware wallet manufacturers provide paper wallet backup solutions that complement the hardware wallet. These paper wallets feature QR codes, which can be scanned to configure the hardware wallet or retrieve funds. This adds an extra layer of security since the private key remains offline. An example of this is the Ledger Nano X paired with Ledger's "Crypto Asset Recovery Pack."
- Mobile Hardware Wallets: Several hardware wallet manufacturers have introduced mobile versions of their products, enabling users to transform their smartphones into secure hardware wallets. These mobile hardware wallets typically come paired with a dedicated mobile app. An example is the Ledger Live mobile app with Ledger hardware wallets.
- Multi-signature Hardware Wallets: Hardware wallets are designed to work in conjunction with others to create multisignature wallets, adding an extra layer of security. Users typically need multiple hardware wallets to sign transactions, making it more challenging for a single compromised device to access funds. Multisignature functionality can be integrated into some standard hardware wallets.
Joe Grand's Case Study in Hardware Wallet Vulnerabilities
Joe Grand is a hardware hacker and a former member of the L0pht group, a collective of hackers who testified before the US Senate in 1998 about the vulnerabilities of the internet. He hacked a Trezor One hardware wallet and recovered $2 million worth of cryptocurrency for a client who forgot his password. [11]
In 2021, Joe Grand, an electrical engineer and inventor, also known by the hacker handle 'Kingpin', was requested to hack Dan Reich's Trezor One hardware wallet, which had $2.5 million worth of Theta tokens. Reich and his friend had misplaced the recovery phrase for their hardware wallet. Initially, they had purchased a batch of Theta tokens in 2018 valued at $50,000. By 2021, the value of this batch had surged to $2.5 million, amplifying the urgency to recover access.[10]
Reich and his friend found a financier in Switzerland who claimed he had associates in France who could crack the wallet in a lab. He’d have to hand off his wallet to the financier in Switzerland, who'd take it to his French associates. The pandemic slowed their plans in 2020, but in February 2021, with the value of their tokens then rising to $2.5 million, Reich was preparing to fly to Europe when suddenly they found a hardware hacker in the US named Joe Grand. Grand, who had a custom lab in his family’s Portland backyard, purchased several identical wallets to the one Reich and his friend owned and installed the same version of firmware on them. Then he spent three months doing research and attacking his practice wallets with various techniques.
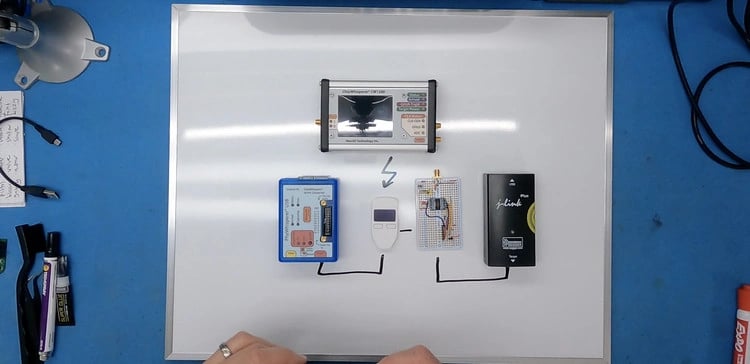
Grand knew a 15-year-old hardware hacker in the UK, Saleem Rashid had developed a method to successfully unlock a Trezor wallet belonging to tech journalist, Mark Frauenfelder and helped him free $30,000 in Bitcoin, in 2017. Rashid found that when the Trezor wallet was turned on, it made a copy of the PIN and key that was stored in the wallet’s secured flash memory and placed the copy in RAM. A vulnerability in the wallet allowed him to put the wallet into firmware update mode and install his own unauthorized code on the device, which let him read the PIN and key where it was in RAM. But the installation of his code caused the PIN and key stored in long-term flash memory to erase, leaving only the copy in RAM.
This made it a risky technique for Grand to use. If he inadvertently erased the RAM before he could read the data, the key would be unrecoverable. Then, they found that at some point during the firmware update mode, the PIN and key were being temporarily moved to RAM to prevent the new firmware from writing over the PIN and key, then moved back to flash once the firmware was installed. So they devised a technique dubbed “wallet.fail.” This attack used a fault-injection method (glitching), to undermine security protecting the RAM and allow them to read the PIN and key when they were briefly in RAM.
By doing a fault injection attack against the chip, the wallet.fail team found they could downgrade the security from RDP2 to RDP1. They could then force the wallet into firmware update mode, sending the PIN and key into RAM, and reading them. It was similar to Rashid’s attack, except the fault injection got them access to RAM without needing to exploit code. Reich then immediately moved the Theta tokens out of their account and sent a percentage of the money to Grand for his services.[10][11]
