Subscribe to wiki
Share wiki
Bookmark
Double Spending Problem
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
0%
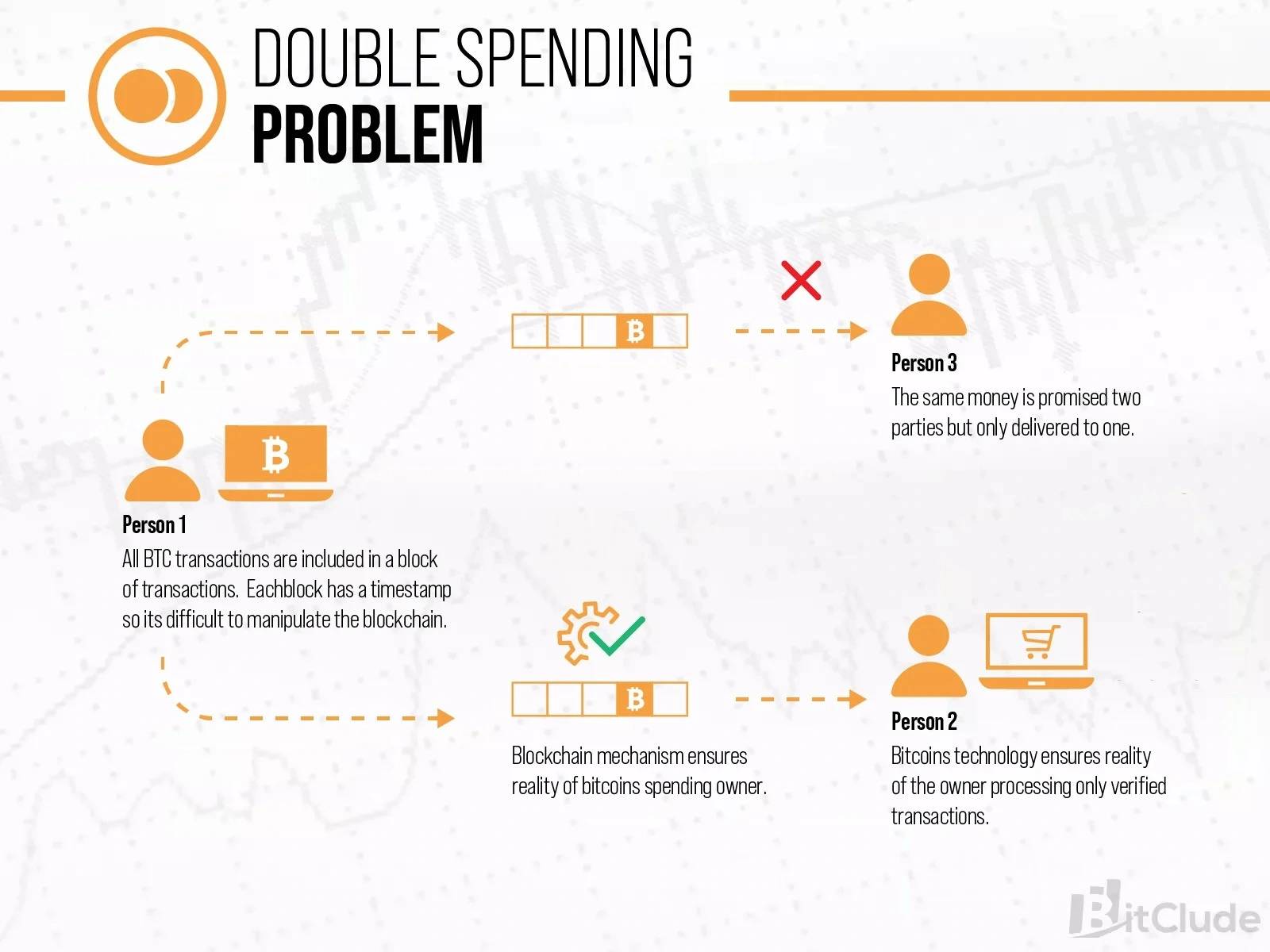
Double Spending Problem
Double spending problem is a phenomenon in which a single unit of currency is spent simultaneously more than once. This creates a disparity between the spending record and the amount of that currency available.Double spending is most commonly associated with Bitcoin because digital information can be manipulated or reproduced more easily by skilled programmers familiar with how the blockchain protocol works. Bitcoin is also a target for thieves to double spend because Bitcoin is a peer-to-peer medium of exchange that doesn’t pass through any intermediaries or institutions.[1]
Overview
For example, if someone walks into a clothing store with only $10 and buys a $10 shirt, then buys another $10 shirt with the same $10 already paid to the cashier. While this is difficult to do with physical money, in part because recent transactions and current owners can be easily verified in real-time, there’s more opportunity to do it with digital currency.Bitcoin’s completely digital currency network is decentralized which means it has no central authority, regulators, or governing bodies to police thieves and hackers. Though traditional security entities don’t monitor the Bitcoin network for double spending, other network defenses have been implemented to combat attacks that would otherwise threaten the network’s consensus mechanism and ledger of transactions, providing confidence to those who invest in Bitcoin.
How does Bitcoin Double-Spending work?
Fundamentally, a double spend consists of a bad actor sending a copy of one transaction to make the copy appear legitimate while retaining the original, or erasing the first transaction altogether. This is possible and dangerous for Bitcoin or any digital currency because digital information is more easily duplicated. There are a few different situations where criminals attempt to double-spend Bitcoin.
Simultaneously sending the same Bitcoin amount twice or more
An attacker will simultaneously send the same bitcoin to two (or more) different addresses. This type of attack attempts to exploit the Bitcoin network’s slow 10-minute block time, in which transactions are sent to the network and queued to be confirmed and verified by miners to be added to the blockchain. In sneaking an extra transaction onto the blockchain, thieves can give the illusion that the original bitcoin amount hasn’t been spent already, or manipulate the existing blockchain and laboriously re-mine blocks with fake transaction histories to support the desired future double spend.
Reverse an already-sent transaction
The attacker sends multiple packets (units of data) to the network to reverse the transactions, to give the illusion they never happened. With this way, the attacker attempts a Bitcoin double spend by reversing a transaction after receiving the counterparty’s assets or services, thus keeping both the received goods and the sent bitcoin.
51% Attack
When a group of miners controls over 50% of the network’s hash rate, they launch a 51% attack against a cryptocurrency blockchain. Having control of 51% of the network’s nodes provides the governing parties with the ability to change the blockchain.Payments between a few or all users might be stopped if the attackers were able to stop fresh transactions from receiving confirmations. The ability to undo decisions taken when they were in charge would likewise be available to them. One of the problems that consensus systems like proof-of-work were designed to avoid is that by reversing transactions, users might double spend coins.On a coin with a high participation rate, a 51% assault is an extremely demanding and difficult undertaking. The majority of the time, the group of attackers would have to be able to command the required 51% and have a backup blockchain ready to be injected when the opportunity arises.The main network would then have to be out-hashed. One of the biggest obstacles against a 51% attack is the expense of doing so. For instance, the Bitmain S19 XP Hydro is the most sophisticated Application Specific Integrated Circuit (ASIC) miner. It boasts 255 TH/s (tera hashes per second) of hash rate and costs more than $19,800.FoundryUSA, with 54.42 EH/s (exahashes per second), accounts for 23.75% of the entire Bitcoin network hash rate, followed by AntPool at 41.49 EH/s, 18.12%, and Binance Pool at 34.48 EH/s, 15.06%.[2]
Finney Attack
The Finney attack is named after Hal Finney, who happened to be the first recipient of a Bitcoin transaction, and the first person to comment on the release of the Bitcoin source code. It is a double spending attack with the following features:
- It only works if the merchant accepts unconfirmed transactions.
- It still works, however, if the merchant waits a few seconds to verify that everyone in the network agrees he was paid.
- It requires the attacker to be mining and controlling the content of his blocks; however, he can in theory do this with any hashrate, in particular significantly less than 50% of the network hashrate.
It proceeds as follows:
- The attacker mines blocks normally. In the block he/she is trying to find, he includes a transaction which sends some of his/her coins back to himself/herself, without broadcasting this transaction.
- When he/she finds a block, he/she does not broadcast it; instead, he/she sends the same coins to a merchant for some goods or service.
- After the merchant accepts the payment and irreversibly provides the service, the attacker broadcasts his/her block. The transaction that sends the coins to himself/herself which is included in this block, will override the unconfirmed payment to the merchant.
If the time from finding the block until the attacker sends payment and the merchant accepts it is 't', and the average time to find a block is 'T', there is a probability of t/T that another block will be found on the network in this time. In this case the attack will fail, and the attacker will lose the block reward of B.This means that the average cost of attempting the attack is about (t/T) * B. As a rule of thumb, the merchant should wait at least t=V*T/B (V is the value of the transaction) to make sure that trying to carry out this attack against him isn't profitable. This may not be sufficient though, as a nimble attacker can use the same block for multiple attacks, potentially gaining the total of their value.The lower the attacker's hashrate, the less opportunities he/she has to carry out the attack. If the attack is for obtaining some illiquid good, it is difficult to make the need for this good coincide with finding a block. If the attack is for obtaining something liquid (e.g. exchanging bitcoins for other money), an opportunity is ever-present but the merchant is likely to require a few confirmations. This makes the attack difficult to use in practice.[4]
Race Attack
The Race Attack is a particular kind of a Double-Spending attempt which is a malicious activity when two transactions are created at the same time using the same funds to spend them twice. It requires the recipient to accept payment for unconfirmed transactions. The attacker sends the victim an unconfirmed transaction. Meanwhile, they broadcast to the network a conflicting transaction. Since the victim observed their own transaction first, they believe they will be paid. However, since the rest of the network saw the double-spend first, it’s likely that the victim will not get the money.Such an attack is significantly easier to carry out when the attacker has a direct connection to the victim's node and deposits the conflicting transaction directly to the miners.[6]
How Double Spending Problem prevented
A timestamp server was suggested as a solution to the double spending issue in Satoshi Nakamoto's white paper. A block of transactions is hashed by this server, which then broadcasts the hash to every node in the bitcoin network. This timestamp demonstrates that none of the information in the hash could have been produced following the publication of the hash. This creates an immutable (unchangeable) log of the sequence in which transactions occurred since each timestamp contains the preceding timestamp in its hash. Each timestamp builds on the ones that came before it.In conclusion, the blockchain stops double spending by broadcasting groups of transactions to all nodes in the bitcoin network and timestamping them. Transactions are irreversible and hard to tamper with since they are timestamped on the blockchain and quantitatively tied to earlier ones.[2]
Bitcoin
Since the first bitcoin client was delivered in 2009, the blockchain of bitcoin has preserved an exhaustive record of all transactions ever done in order to properly comprehend how the blockchain avoids double spending. No one can alter the record since every transaction is cryptographically hashed to the preceding blocks. This database is referred to as a blockchain because a fresh batch of transactions, known as a block, is added to it every ten minutes.
Ethereum
Avoiding double spending means to stop using the same amount twice. If the nonce is set to the same only one of the transactions will be mined and most of the time that can be the one with higher gas price, but however no double spend will happen as only one transaction will take place at the end in either case.[3]There are two types of nonce used in Ethereum.
- Account nonce It's simply the transaction count of an account. This prevents replay attacks where a transaction sending, for example, 20 coins from A to B can be replayed by B over and over to continually drain A's balance.
- Proof of work nonce The random value in a block that was used get the proof of work satisfied (depending on the difficulty at the time). Proof of work nonce is a meaningless value in a block which can be adjusted in order to try to satisfy the proof of work condition.
Cases
In December of 2019, a viral video showcased bitcoin being double-spent at locations that accept bitcoin. These attacks were made possible using Replace-By-Fee (RBF), a somewhat controversial upgrade to the Bitcoin protocol. The first transaction was sent to the merchant, followed by a second transaction with a higher fee attached. This RBF transaction overrode the first transaction as the higher fee meant it would be processed preferentially, allowing it to be double-spent. These attacks worked because the merchants accepted unconfirmed transactions.
In a similar incident earlier in the same year, some Canadian bitcoin holders were able to “cash in” their bitcoin without actually cashing it in. It appeared they sent bitcoin to Bitcoin ATMs, where they were able to withdraw cash. After receiving the cash, they cancelled the transactions, since they had yet to be “confirmed.” [5]
See something wrong?
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)