Subscribe to wiki
Share wiki
Bookmark
Trusted Execution Environments
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
0%
Trusted Execution Environments
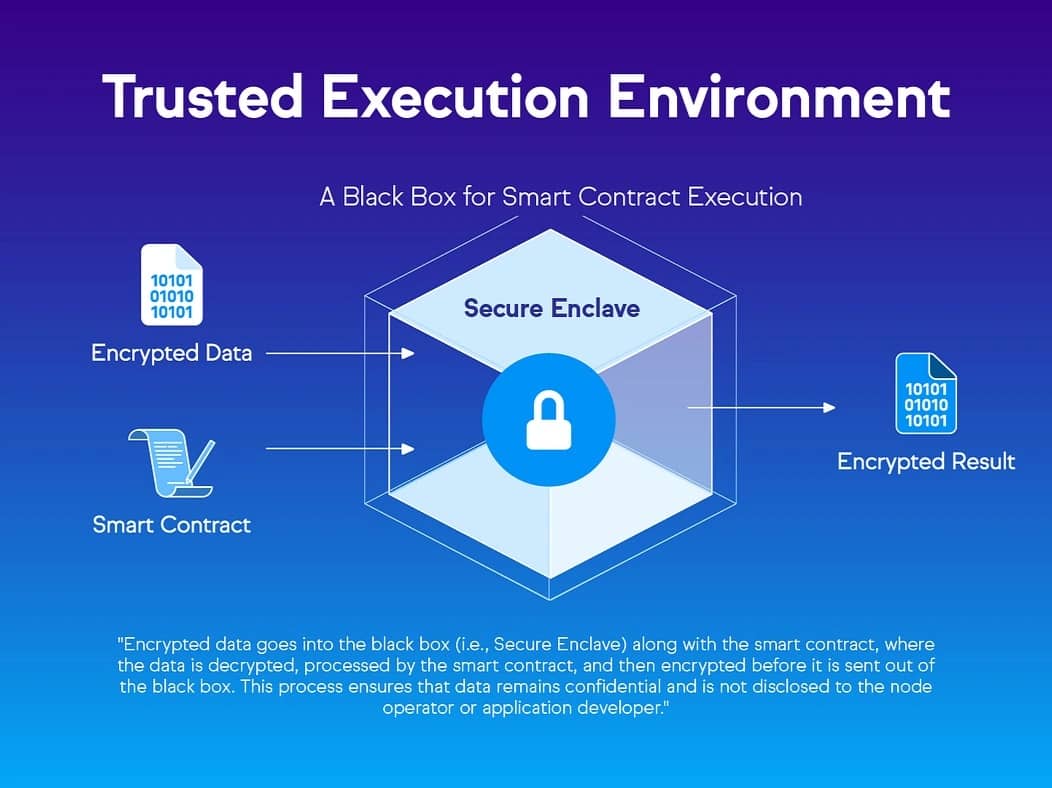
Trusted Execution Environments (TEEs) are secure, isolated areas within a computer's main processor designed to protect code and data with respect to confidentiality and integrity. Also known as enclaves, TEEs provide a hardware-enforced barrier that separates sensitive computations from the host system's operating system, hypervisor, and other applications, ensuring that data remains protected even from an administrator with full control over the machine. [1] [2]
Overview
The core purpose of a Trusted Execution Environment is to enable the secure execution of code and confidential processing of data. This is achieved through hardware-level isolation, which creates a protected container inaccessible to any software outside the enclave, including the host operating system. The security of a TEE is anchored by a "hardware root of trust," which typically involves immutable private keys embedded into the processor during manufacturing, preventing the environment from being simulated or compromised by user-controlled software. [3]
The technology first emerged in the 1990s for applications such as digital rights management (DRM) and secure payments. [1] The concept was more formally defined in the mid-2000s by the Open Mobile Terminal Platform (OMTP) in its "Advanced Trusted Environment: OMTP TR1" standard. [3] In recent years, TEEs have gained significant traction in the blockchain and Web3 sectors as a practical solution for implementing privacy, enhancing scalability, and mitigating security risks like Maximal Extractable Value (MEV). [4]
TEEs are often compared to purely cryptographic privacy solutions like Zero-Knowledge Proofs (ZKPs) and Fully Homomorphic Encryption (FHE). While ZKPs offer a "trustless" model based on mathematical proofs, TEEs rely on trust in the hardware manufacturer. However, TEEs are generally considered more performant and flexible for general-purpose computation, capable of running existing applications without requiring bespoke domain-specific languages or complex proof systems. [1] [3]
Technology
Core Principles
The functionality of TEEs is built on several key principles that collectively provide a secure computing environment:
- Confidentiality: Code and data loaded inside the TEE are encrypted in memory. They are inaccessible to any software outside the enclave, including the host operating system, kernel, or hypervisor.
- Isolation: Hardware-level separation prevents the host system from accessing or interfering with processes running inside the TEE. The TEE enforces strict memory access controls, and any attempt by the host OS to read the TEE's protected memory is blocked by the hardware.
- Attestability: A TEE can generate a cryptographic proof, known as an "attestation," of its origin and the exact code it is executing. This allows a remote third party to verify that a computation was performed by a genuine TEE running trusted, untampered software. [1]
Mechanism of Operation
The lifecycle of code and data within a TEE involves several hardware-managed steps to ensure security from boot to exit:
- Initialization: At system boot, the BIOS/UEFI initializes the hardware and allocates a region of memory for the TEE. A dedicated Memory Encryption Engine (MEE) encrypts this RAM region.
- Loading: Encrypted code and data are loaded from storage into the TEE's protected memory, where they are decrypted for use only within the enclave.
- Execution: An application enters the enclave using special CPU instructions, a process analogous to the switch from user mode to kernel mode in a traditional operating system.
- Interaction: Since peripherals like storage and network cards are outside the TEE's trust boundary, all I/O operations are handled via shared memory. Data entering the TEE from these untrusted components must be validated. For secure network communication, a TEE can generate its own key pair internally to establish a Transport Layer Security (TLS) session.
- Exiting: The TEE uses secure APIs or exit functions to interact with non-TEE resources. [1]
Remote Attestation
Remote attestation is a critical feature that allows a TEE to prove its integrity to a remote party. The process typically involves four steps:
- Measurement: The CPU measures the Trusted Computing Base, which includes the boot firmware, operating system, and application binaries.
- Storage: This measurement is stored in secure hardware registers within the CPU.
- Signing: The CPU signs the measurement using a unique, private attestation key that was embedded in the hardware during manufacturing.
- Verification: The signed measurement, or "attestation report," is sent to a remote verifier. The verifier can check the signature to confirm the enclave's authenticity and verify that the correct code is being executed. [2]
Key Implementations
Several major hardware manufacturers have developed their own TEE technologies:
- Intel: Software Guard Extensions (SGX) and its successor, Trust Domain Extensions (TDX).
- AMD: Secure Encrypted Virtualization (SEV).
- ARM: Confidential Compute Architecture (CCA).
- NVIDIA: Enclaves on its Hopper and Blackwell GPU architectures. [1]
Use Cases
Traditional and Web2 Applications
Before their adoption in blockchain, TEEs were widely used in various sectors to protect sensitive data and intellectual property:
- Digital Rights Management (DRM): Protecting high-value content like 4K movies and premium audio from unauthorized copying.
- Financial Services: Securing mobile wallets, contactless payments, and point-of-sale (POS) terminals.
- Authentication: Providing a secure environment for biometric data processing, including facial recognition, fingerprint scanning, and voice authorization, similar to Apple's Secure Enclave in iPhones.
- Enterprise and Government: Handling confidential information securely on mobile devices and server infrastructure. [3] [5]
Web3 and Blockchain Applications
TEEs offer solutions to several key challenges in the blockchain space, including privacy, scalability, and security. As of September 2025, over 50 teams were reported to be actively working on TEE-based blockchain projects. [2]
Private Smart Contracts
TEEs enable the creation of confidential smart contracts where the logic, data inputs, and state remain private from the public and even from the node operators running the network. This allows for applications that handle sensitive information, such as healthcare or financial data, on-chain. A node operator's TEE can execute computations on this private data without having access to the data itself. [1]
"TEEs enable node operators to participate in a network without knowledge of the private data that is being processed on their server." [1]
Scalability and Off-chain Computation
Computationally intensive tasks can be offloaded from a main blockchain to TEE-enabled nodes. These nodes execute the tasks securely off-chain and submit only the results and a proof of correct execution back to the chain. This reduces network load and transaction costs, thereby increasing throughput. This model is used in some Layer 2 scaling solutions and decentralized cloud computing platforms. [3]
MEV Mitigation
Maximal Extractable Value (MEV) refers to the profit that can be extracted from a blockchain by reordering, inserting, or censoring transactions. TEEs are being implemented to combat MEV by creating private transaction pools and verifiable block builders. In such a system, users submit their transactions to a block builder running its operations inside a TEE. The TEE ensures the transaction data remains confidential until it is finalized in a block, preventing MEV searchers from front-running or sandwiching the transaction. This approach aims to solve the "MEV trilemma" by creating a system that is simultaneously fast, decentralized, and private. [5]
Secure Oracles and Interoperability
TEEs can provide a secure environment for oracle computations, ensuring the integrity of external data being fed into smart contracts. They can also function as trusted intermediaries to facilitate secure data exchange and asset transfers between different blockchain networks, enhancing cross-chain interoperability. [3]
Implementations and Adoption
Numerous projects across the Web3 ecosystem have integrated TEEs into their architecture:
- Secret Network: The first blockchain to launch with private smart contracts by default, using Intel SGX. It is built with the Cosmos SDK and enables confidential states and transactions.
- Oasis Network: A platform that uses TEEs to power Sapphire, its confidential EVM-compatible ParaTime, enabling private dApps on an Ethereum-like environment.
- Unichain: An optimistic rollup developed by the Uniswap team, launched in October 2024. It uses TEEs (initially Intel TDX) in its block-building process, in collaboration with Flashbots, to create an MEV-resistant infrastructure.
- Flashbots: A research organization focused on MEV that is developing a "verifiable block builder" (rollup-boost) that utilizes TEEs. This technology is a core component of Unichain's design.
- iExec: A decentralized cloud computing platform that uses Intel SGX for secure off-chain computation.
- Scroll and Taiko: Ethereum rollups that use TEEs as a second type of prover alongside ZK provers to add redundancy and enhance security. Other notable projects include Cycles Protocol, Automata, Phala, and Marlin. [2] [5] [4]
Challenges and Limitations
Despite their utility, TEEs are subject to significant challenges and criticisms related to their security model and reliance on centralized hardware.
Vendor Trust and Centralization
The entire security model of a TEE relies on trust in the hardware manufacturer (e.g., Intel, AMD). This introduces a centralized point of failure and runs counter to the decentralization ethos of many blockchain projects. There is a risk that a manufacturer could be compelled by a government agency to introduce a backdoor or that a flaw could be introduced in the complex supply chain. [2] [3]
Security Vulnerabilities
TEEs have been proven vulnerable to several classes of attacks that can compromise their confidentiality and integrity guarantees.
- Side-Channel Attacks: These attacks extract information by observing patterns in hardware operations. Examples include Spectre, which exploits speculative execution, and Plundervolt, which manipulates CPU voltage to induce faults inside an SGX enclave and extract secrets.
- Microprocessor Vulnerabilities: TEEs are susceptible to general hardware bugs like Meltdown.
- Physical Attacks: Research has indicated that no existing TEE design can fully defend against a sophisticated attacker with physical access to the chip.
- Implementation Bugs: Flaws in the TEE's isolation mechanisms or the software running inside can compromise its security. Intel's SGX technology, for instance, has a documented history of vulnerabilities compiled on websites like "sgx.fail". [1] [5]
Daniel Shapiro of Blockworks Research noted the risks for protocols like Unichain, stating, "As the chain grows, the incentive to attack will grow in unison. New security exploits could arise that could put user funds at risk." [5]
Risk Mitigation and Research
To address the inherent limitations of TEEs, developers and researchers have proposed various mitigation strategies and are exploring next-generation designs.
Best Practices for Implementation
Developers are advised to design systems with the assumption that TEEs can eventually be compromised.
- Design for Failure: Systems should be architected so that a TEE exploit is a "nuisance, not an existential risk." For example, TEEs should not be the sole component protecting a system's integrity.
- Privacy over Integrity: TEEs are better suited for confidentiality. Using them as the sole mechanism for integrity-critical tasks like transaction validation is discouraged, as a compromise could allow an attacker to falsify assets.
- Oblivious RAM (ORAM): This technique can be used to obscure memory access patterns when the TEE interacts with host RAM, mitigating side-channel leaks at the cost of performance.
- Forward Secrecy and Key Rotation: Regularly replacing encryption keys limits the impact of a compromise, as a stolen key cannot be used to decrypt past data protected by older keys. [1]
Distributed Key Management
To prevent a single point of failure, TEE-based systems often employ distributed key management. The Ekiden protocol pioneered a model where a "Key Management Committee" (KMC) composed of trusted nodes manages sensitive keys using threshold cryptography. The KMC issues short-lived, limited-access keys to individual worker nodes, which must prove their legitimacy via remote attestation to receive them. This system includes proactive key rotation to further enhance security. [2]
Future Research Directions
Research is underway to develop TEEs that do not require trusting the manufacturer. Proposed solutions include using Physical Unclonable Functions (PUFs) to secure the root-of-trust, incorporating masking techniques to protect computations from physical attacks, and building TEEs with open-source hardware and formally verified, reproducible builds to ensure design integrity. [4]
See something wrong?
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)