Subscribe to wiki
Share wiki
Bookmark
Consensus Mechanism
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)
0%
Consensus Mechanism
A Consensus Mechanism is a protocol that facilitates agreement among all nodes within a distributed blockchain network regarding a unified data set. These mechanisms serve as the criteria for validating and approving each transaction on the blockchain. [1][2]
Overview
A consensus mechanism is used in blockchains to maintain distributed agreement about the state of a ledger. Consensus mechanisms are generally implemented in blockchain networks with many users and processes. They serve as benefits for cryptocurrencies and blockchains because they replace slower human verifiers and auditing. [3]
Consensus mechanisms are essential for ensuring the security, reliability, and validity of the blockchain, as they prevent malicious attacks, data tampering, and double-spending.
A consensus is achieved on the Ethereum blockchain when at least 66% of the nodes in the network are in agreement with the overall state of the network. Ethereum employs a proof-of-stake-based consensus mechanism, which derives its crypto-economic security from a system of rewards and penalties associated with the capital staked by participants. This incentive framework promotes honest validation by individual stakers, penalizes those who act dishonestly, and imposes a significant cost on attempts to compromise the network's integrity. Bitcoin on the other hand uses a Proof-of-Work (PoW) mechanism. This mechanism requires computational power to solve an encrypted puzzle (or hash). [1][3]
Types of Consensus Mechanisms
Blockchain platforms have continually refined and adapted consensus protocols in their quest for the ideal balance between decentralization, scalability, and security. As a result, a collection of methodologies has emerged to support Web3 applications. Here are the four most frequently encountered consensus practices:
Proof of Work (PoW)
Proof of Work (PoW) involves miners solving complex cryptographic puzzles, called a hash, to validate transactions and add blocks to the blockchain. The difficulty of the puzzle adjusts according to the network’s hash rate, which is the combined computing power of the nodes. It's known for its robust security but is energy-intensive and less scalable. The network remains secure due to the requirement of having 51% of the network's computational power to compromise the blockchain. Achieving this would necessitate substantial investments in equipment and energy, potentially resulting in costs outweighing potential gains.[1][4][5] Proof of Work (PoW) is used by Bitcoin and Dogecoin for their BTC and DOGE cryptocurrencies. [8]
Pros: PoW is one of the most decentralized and secure verification mechanisms, known for its high reliability. In the case of Bitcoin, a substantial block validation reward has incentivized active participation on the platform.[5]
Cons: The downsides of the PoW consensus mechanism include slower transaction rates, costly gas fees, expensive operational expenses, and environmentally harmful energy consumption. Bitcoin's average block time, which signifies the time required to process a transaction, is 10 minutes, and the energy consumption involved is considerable.[4][5]
Proof of Stake (PoS)
PoS is the mechanism that Ethereum started to use after the Merge. In Proof of Stake (PoS), validators are chosen to create new blocks based on the amount of cryptocurrency they hold and are willing to "stake" as collateral. PoS is more energy-efficient compared to PoW but requires participants to have a stake in the network. Hence, the responsibility of maintaining the public ledger is based on the number of crypto assets held. The more tokens a node stakes, the higher its chances of being selected as a block proposer or validator. [3][6][7]
Pros: Regarded as the preferred consensus method in Web3 for enhancing scalability. It is known for its energy efficiency and cost-effectiveness, particularly concerning gas fees and equipment requirements.[5]
Cons: Falls short in terms of decentralization and security compared to proof of work. Delegation of power is based on wallet size. It also introduces new challenges such as the risk of losing staked tokens due to penalties or attacks.[1][5][6]
Delegated Proof of Stake (DPoS)
DPoS introduces a voting system where token holders select a small group of delegates to validate transactions. Consequently, validation privileges are selectively assigned and periodically reassigned to a select group of top-tier candidates. Any validator can potentially be replaced by someone deemed more trustworthy at any given time. This approach enhances scalability and speed but relies on a smaller number of trusted validators. Projects that use DPoS include BitShares, TRON, Steem, Lisk, Ark, and EOS. [5][9][10]
Pros: This system is characterized by its efficiency and democratic nature. It enhances the original proof-of-stake method by being more financially inclusive to users and provides incentives for validators to maintain accountability in sustaining the network. DPoS is reputation-based, fast, scalable, and requires minimal hardware compared to the original proof of stake. [5][10]
Cons: Notable downsides of DPoS include a lack of decentralization, engagement requirements, and possibly malicious token holders. [10]
Proof of Authority
This is a mechanism that relies on a set of trusted nodes, called authorities, to validate transactions and blocks. The authorities are chosen based on their reputation, identity, or other criteria. The PoA consensus process confers authority upon a select group of blockchain participants to validate network transactions and make updates to its widely dispersed ledger. The algorithms operate in a straightforward manner, with designated parties taking turns as the mining leader, responsible for generating new blocks upon which distributed consensus is achieved. PoA is adopted by VeChain, Ethereum Kovan Testnet, JP Morgan (JPMCoin), and Xodex. [1][11]
Pros: PoA mechanism is highly scalable and does not require computing power. It also provides a fast and low-cost way to achieve consensus. [5]
Cons: Validators on projects with Proof of Authority (PoA) lose their pseudo-anonymity since public identifiability is an integral part of their role. It also sacrifices some degree of decentralization and security.[5]
Practical Byzantine Fault Tolerance (PBFT)
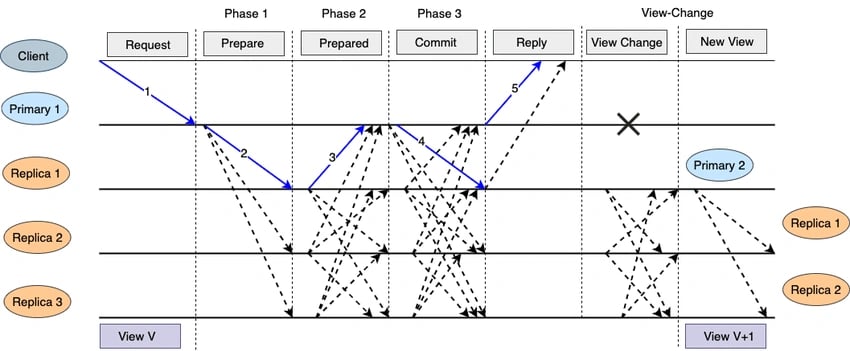
However, the security of PPFT will be breached if the dishonest nodes are more than ⅓ of all the nodes in the network. The nodes in PBFT are divided into primary and secondary nodes. The primary nodes are the leader nodes, while the secondary nodes are the backup nodes. The primary nodes are changed at every consensus round.[12]
Pros: Energy efficiency and high throughput
-
Energy Efficiency: PBFT does not require any power consumption or high-level computational power, unlike PoW. This enhances its efficiency and makes it easier to run.
-
High Throughput: BPFT mechanisms can handle high throughput conveniently as the nodes quickly interact and validate transactions. The decisions of the nodes are final, so there is no need for block finality confirmation. Disputes among the nodes are also resolved quickly in case they contest the validity of any block.
Cons: Not scalable and susceptible to sybil attacks
-
Not Scalable: PBFT was primarily designed for not-too-large blockchains. Thus, it is not scalable for larger blockchains due to the intense back-and-forth communication among the nodes. As the number of transactions increases, it will take more time to agree on and approve them.
-
Susceptible To Sybil Attack: A typical Sybil Attack occurs when a single person or group is in charge of several dishonest nodes in the network. If the dishonest nodes are more than the honest nodes, they can manipulate and take over the chain.
See something wrong?
The Agent Tokenization Platform (ATP):Build autonomous agents with the Agent Development Kit (ADK)